Most british businesses discover too late that weak authentication leaves critical data exposed. Cybercriminals target small and medium enterprises across the United Kingdom because single passwords are easy to steal or guess. Two-factor authentication stops over 99 percent of account compromise attempts, offering british companies a powerful defence for cloud-based systems. Learn how practical, user-friendly verification can protect your organisation and keep private business data secure from modern threats.
Table of Contents
- Two-Factor Authentication Explained For Businesses
- Common Methods Used In Modern Authentication
- How Two-Factor Authentication Works In Practice
- Risks Of Weak Authentication And Common Pitfalls
- Legal Compliance And Best Practices In The UK
Key Takeaways
| Point | Details |
|---|---|
| Importance of Two-Factor Authentication (2FA) | 2FA significantly enhances security by requiring two validation methods, reducing the risk of unauthorised access. |
| Diverse Authentication Methods | Businesses can implement various methods like SMS codes, biometric verification, and hardware tokens to accommodate different user preferences. |
| Legal Compliance | UK SMEs must adhere to regulations requiring robust authentication practices to protect sensitive data and avoid potential penalties. |
| Risks of Weak Security Practices | Reusing passwords and neglecting security training can lead to vulnerabilities that cybercriminals exploit, making proactive measures essential. |
Two-factor authentication explained for businesses
Two-factor authentication (2FA) is a critical security mechanism that protects businesses from increasingly sophisticated cyber threats. By requiring users to provide two separate verification methods before accessing digital systems, 2FA creates a robust defence against unauthorised access. Unlike traditional single-password approaches, this method significantly reduces the risk of security breaches.
The core principle of two-factor authentication involves combining two distinct authentication factors from different categories. Multifactor authentication strategies typically involve something the user knows (like a password), something the user possesses (such as a mobile device), or something inherent to the user (like a fingerprint). For UK small and medium enterprises, this means creating multiple layers of digital protection that make it exponentially harder for cybercriminals to compromise sensitive business data.
Businesses implementing 2FA can choose from several authentication methods, including:
- SMS-based verification codes
- Authentication mobile apps
- Hardware security tokens
- Biometric verification like fingerprint or facial recognition
- Email-based secondary confirmation
While adding an extra authentication step might seem inconvenient, the security benefits far outweigh minor user friction. Implementing 2FA can reduce the likelihood of account compromise by up to 99.9% compared to traditional password-only systems. For UK SMEs handling sensitive customer data, financial information, and business intelligence, this additional security layer is not just recommended but increasingly essential.
Pro tip: Select a 2FA solution that offers multiple verification methods to accommodate different user preferences and technological capabilities.
Common methods used in modern authentication
Modern authentication technologies have evolved significantly beyond traditional password-based systems. Authentication mechanisms now incorporate multiple layers of security to protect digital identities and prevent unauthorised access. These methods typically fall into three primary categories: something the user knows, something the user possesses, and something inherent to the user.
The most common authentication methods include:
- Password-based authentication: Traditional method requiring users to enter a unique combination of characters
- Token-based authentication: Physical or digital devices generating temporary access codes
- Biometric authentication: Using unique physical characteristics like fingerprints, facial recognition, or retinal scans
- Smart card authentication: Using microchip-embedded cards that store encrypted user credentials
- Risk-based authentication: Dynamically assessing login attempts based on contextual factors like device, location, and user behaviour
Each authentication method offers distinct advantages and potential vulnerabilities. Passwords remain widespread but are increasingly considered weak due to human tendencies like reusing credentials across platforms. Biometric methods provide higher security by leveraging unique physiological characteristics that cannot be easily replicated. Hardware tokens and smart cards add an additional physical verification layer, making remote attacks substantially more challenging.
Businesses must carefully evaluate their specific security requirements when selecting authentication approaches. Combining multiple methods through multi-factor authentication provides the most robust protection against potential cyber threats. By implementing a nuanced, layered approach, organisations can significantly reduce the risk of unauthorized system access while maintaining user convenience.
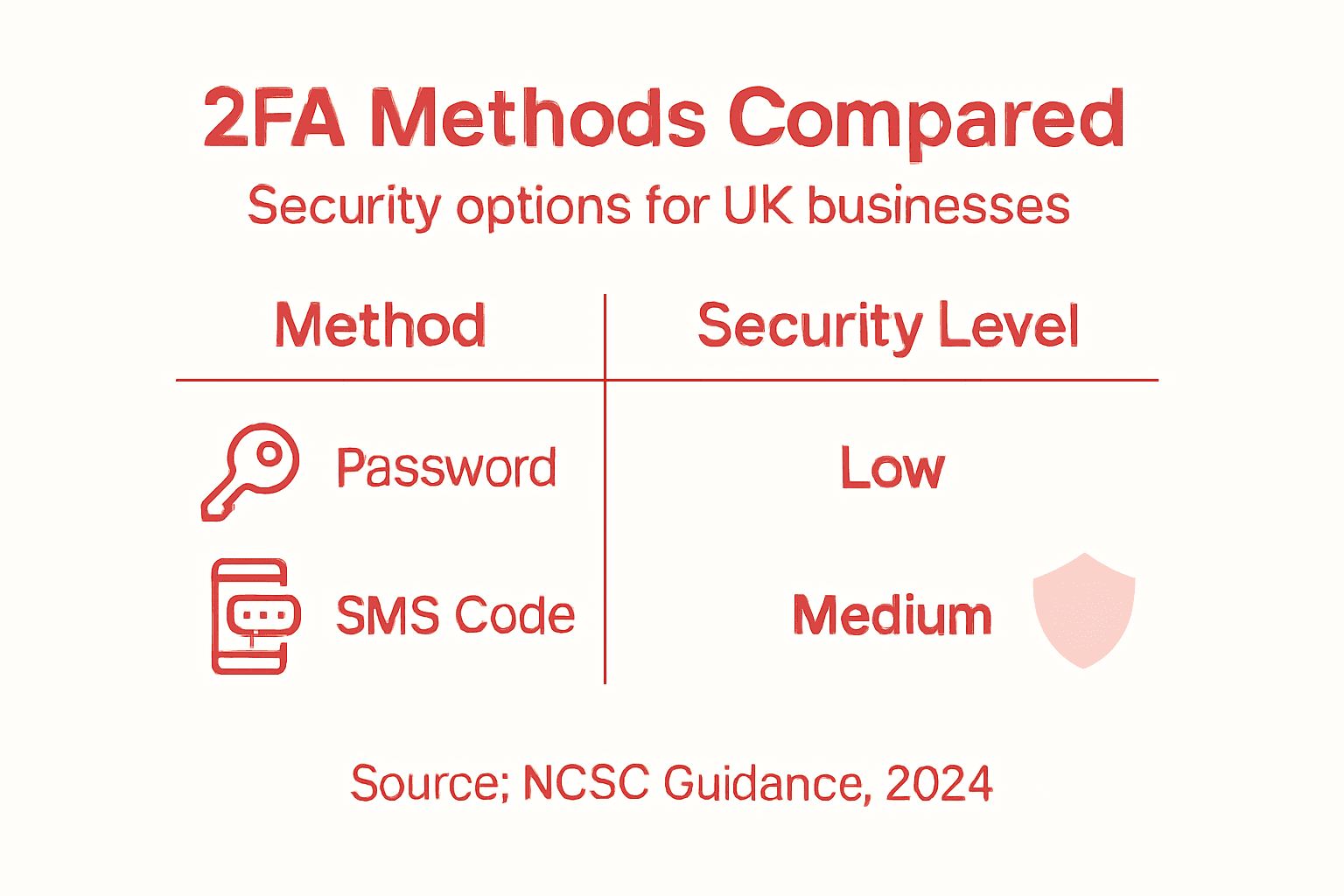
Here’s how common authentication methods compare for UK businesses:
| Method | Security Level | User Convenience | Typical Use Case |
|---|---|---|---|
| Passwords | Low to moderate | High | Everyday logins |
| Hardware tokens | High | Moderate | Sensitive system access |
| Biometric verification | Very high | High | Mobile device and terminal use |
| Smart cards | High | Moderate | Physical office environments |
| Risk-based systems | Variable (adaptive) | High | Protecting online services |
Pro tip: Regularly update and rotate authentication credentials, and implement adaptive authentication systems that can dynamically adjust security protocols based on detected risk levels.
How two-factor authentication works in practice
Two-factor authentication transforms digital security by creating a sophisticated verification process that extends far beyond traditional password protection. Two-factor authentication mechanisms typically involve a sequence of identity confirmation steps designed to dramatically reduce the risk of unauthorized access.
The practical implementation of 2FA follows a structured approach:
- Initial login stage: User enters standard username and password
- Secondary verification: System requires an additional authentication factor
- Verification methods:
- One-time SMS codes
- Authentication mobile application codes
- Biometric confirmation (fingerprint or facial recognition)
- Hardware security token validation
- Email-based verification links
The core strength of two-factor authentication lies in its requirement for independent verification methods. A potential cybercriminal would need to compromise multiple authentication layers simultaneously, which is exponentially more challenging than cracking a single password. This approach means that even if a password is stolen or guessed, the additional verification step creates a robust barrier against unauthorized system entry.
For UK small and medium enterprises, implementing 2FA represents a critical security strategy. The process involves configuring systems to demand two distinct forms of identification, typically combining something the user knows (password) with something the user possesses (mobile device or security token). By introducing this additional verification layer, businesses can significantly mitigate the risks associated with credential theft, phishing attacks, and unauthorized network access.

Pro tip: Implement a flexible 2FA system that allows users to select from multiple verification methods while maintaining stringent security protocols.
Risks of weak authentication and common pitfalls
Small and medium enterprises face significant cybersecurity challenges, with authentication bypass vulnerabilities representing a critical point of potential system compromise. Weak authentication mechanisms create opportunities for sophisticated cybercriminals to exploit network security, potentially resulting in devastating data breaches, financial losses, and operational disruption.
The most common authentication pitfalls for UK businesses include:
- Reusing passwords across multiple platforms
- Implementing single-factor authentication
- Neglecting regular password rotation
- Insufficient employee cybersecurity training
- Failing to monitor suspicious login attempts
- Using default or easily guessable credentials
- Not implementing multi-factor authentication
Cybercriminals exploit these vulnerabilities through various sophisticated techniques. Credential stuffing attacks, where hackers use stolen username and password combinations across multiple systems, can rapidly compromise entire network infrastructures. Brute force attacks systematically attempt numerous password combinations, taking advantage of weak authentication protocols. Small businesses are particularly vulnerable because they often lack comprehensive cybersecurity resources and dedicated IT security teams to implement robust protective measures.
The financial and reputational consequences of weak authentication can be catastrophic. A single successful breach can result in significant data loss, regulatory penalties, customer trust erosion, and potential business closure. UK small and medium enterprises must recognise that cybersecurity is not an optional investment but a critical business survival strategy.
Pro tip: Conduct regular security audits and implement comprehensive employee training programmes to identify and address authentication vulnerabilities before they can be exploited.
Legal compliance and best practices in the UK
UK small and medium enterprises face increasingly stringent legal requirements surrounding digital security and identity verification. Identity verification requirements are becoming more complex, with new regulations mandating robust authentication practices to prevent economic crime and protect sensitive business information.
Key legal compliance considerations for UK businesses include:
- Adherence to the Economic Crime and Corporate Transparency Act
- Implementing multi-factor authentication
- Protecting personal and corporate data under UK GDPR
- Regular security audits and vulnerability assessments
- Maintaining comprehensive access control logs
- Ensuring secure user authentication protocols
- Protecting against unauthorized system access
The UK National Cyber Security Centre provides clear guidance for businesses seeking to meet regulatory standards. Companies must demonstrate a proactive approach to cybersecurity, with two-factor authentication emerging as a critical component of legal compliance. Failure to implement adequate security measures can result in significant penalties, including potential fines, legal action, and reputational damage. Small businesses are particularly vulnerable, as cybercriminals often target organisations with perceived weak security infrastructures.
Beyond legal requirements, implementing robust authentication practices represents a strategic business decision. By adopting comprehensive security protocols, UK SMEs can protect their digital assets, maintain customer trust, and demonstrate professional commitment to data protection. The evolving regulatory landscape demands continuous adaptation and investment in cybersecurity technologies and practices.
Summary of major UK legal requirements for digital authentication:
| Regulation or Standard | Main Focus | Impact on SMEs |
|---|---|---|
| Economic Crime & Transparency Act | Preventing fraud and misuse | Mandatory identity verification |
| UK GDPR | Data protection and privacy | Ensuring secure data access |
| NCSC Guidance | Cybersecurity best practices | Recommending strong authentication |
| Access Control Policies | User access management | Limiting credentials exposure |
Pro tip: Develop a comprehensive authentication policy that not only meets current legal requirements but anticipates future regulatory changes and emerging security threats.
Strengthen Your Business Security with Trusted IT Solutions
Two-factor authentication is essential for UK SMEs aiming to defend against cyber threats and comply with legal requirements. If your business struggles with weak authentication practices, password reuse, or the risks of single-factor access, it is time to take control of your digital security. Implementing robust 2FA and layered authentication methods can prevent costly breaches and safeguard your customer and corporate data.
At Cloudology.uk, we specialise in delivering comprehensive IT services designed to simplify security management and enhance productivity. Our solutions include secure cloud hosting, expert IT support, and tailored network security strategies that incorporate the latest in multi-factor authentication technologies. Do not leave your business vulnerable. Visit Cloudology.uk now to discover how our professional IT services can protect your organisation and ensure compliant, scalable security. Take the first step to secure your SME with trusted experts today.
Frequently Asked Questions
What is two-factor authentication (2FA)?
Two-factor authentication (2FA) is a security mechanism that requires users to provide two separate verification methods before accessing digital systems, adding an extra layer of protection against unauthorized access.
Why do small and medium enterprises (SMEs) need 2FA?
SMEs need 2FA to significantly reduce the risk of security breaches. It helps protect sensitive customer data, financial information, and prevents unauthorized access by adding an additional verification step beyond just passwords.
What methods can be used for two-factor authentication?
Common methods for 2FA include SMS-based verification codes, authentication mobile apps, hardware security tokens, biometric verification (like fingerprints or facial recognition), and email-based secondary confirmation.
How does 2FA enhance security compared to traditional password systems?
2FA enhances security by requiring two independent verification factors, making it exponentially more difficult for cybercriminals to gain unauthorized access. Even if a password is compromised, the additional layer of verification acts as a strong barrier against breaches.

